F5 CVE-2024-39778 (K05710614)
Check if your F5 BIG-IP load balancer device is vulnerable to the HSB vulnerability CVE-2024-39778 (K05710614)
F5 Security Advisory Reference
https://my.f5.com/manage/s/article/K05710614
Security Advisory Description
When a stateless virtual server is configured on a BIG-IP system with a High-Speed Bridge (HSB), undisclosed requests can cause virtual servers to stop processing client connections and the Traffic Management Microkernel (TMM) to terminate. (CVE-2024-39778)
Impact
Traffic is disrupted while the system automatically reboots. This vulnerability allows a remote unauthenticated attacker to cause a denial-of-service (DoS) on the BIG-IP system. There is no control plane exposure; this is a data plane issue only.
On vCMP guests, the automatic reboot may not resolve the issue and traffic may be disrupted until you manually reboot the vCMP host. On systems not configured for vCMP, the automatic reboot resolves the issue.
Prerequisites
- A virtual / physical F5 BIG-IP device
- SSH / console access to the F5 BIG-IP with administrator privileges to enter the bash shell
Steps
- Log in to the F5 BIG-IP via SSH / Console
- Verify the TMOS software version
show sys version
root@(BIGIP-1)(cfg-sync In Sync)(Active)(/Common)(tmos)# show sys version
Sys::Version
Main Package
Product BIG-IP
Version 17.1.1.3
Build 0.0.5
Edition Point Release 3
Date Thu Mar 21 04:23:27 PDT 2024
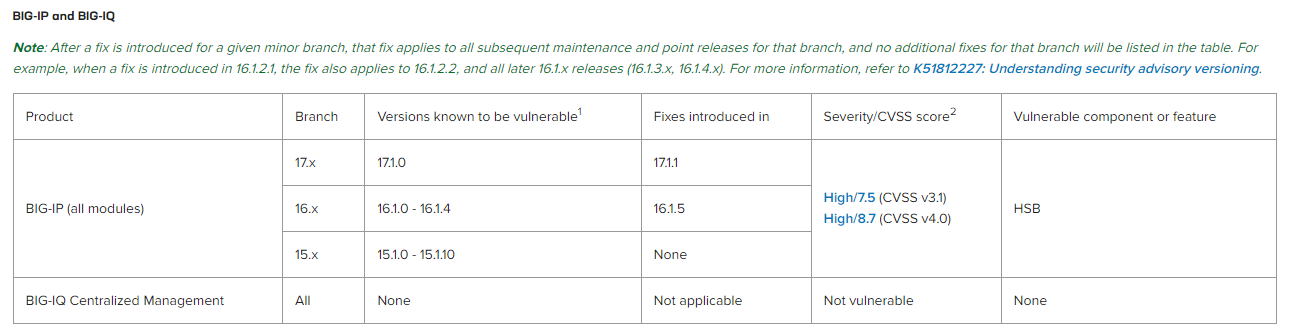
- Check if the TMOS software version matches one of the versions known to be vulnerable as per the table below (click here for the latest tabular information)
- Enter the bash shell
run util bash - Count the number of UDP stateless virtual servers
tmsh -q -c "cd / ; list /ltm virtual recursive one-line" | grep "stateless" | wc -l
* NOTE: This output shows that there is one stateless virtual server configured
[root@BIGIP-1:Active:In Sync] config # tmsh -q -c "cd / ; list /ltm virtual recursive one-line" | grep "stateless" | wc -l
1
- List the names of all UDP stateless virtual servers (if any are configured)
tmsh -q -c "cd / ; list /ltm virtual recursive one-line" | grep "stateless" | awk '{print $3}';
* NOTE: This output shows that there is one stateless virtual server configured with the name of "Common/VS-DELETEME"
[root@BIGIP-1:Active:In Sync] config # tmsh -q -c "cd / ; list /ltm virtual recursive one-line" | grep "stateless" | awk '{print $3}';
Common/VS-DELETEME
- If the results of these checks show that you have a UDP stateless virtual server configured then you will need to perform a code upgrade to the corresponding fixed TMOS software version (currently 16.1.5 / 17.1.1)